What Is DevSecOps?
DevSecOps, short for Development Security Operations, constitutes an organizational framework focused on establishing a continuous integration and delivery cycle that seamlessly integrates application development with security and operational considerations. The key element in this model is the utilization of automation, primarily through infrastructure as code (IaC), to facilitate a smooth software development lifecycle (SDLC).
The primary objective of DevSecOps is to incorporate security measures, including scanning, monitoring, and remediation, throughout the entire SDLC. This comprehensive approach spans all stages, encompassing planning, development, building, testing, release, deployment, ongoing operations, and updates. By doing so, organizations can mitigate security and compliance costs while accelerating the delivery of secure software.
A fundamental tenet of DevSecOps is the collective responsibility of all individuals involved in the planning, development, or delivery of software for security considerations. This entails making security an integral part of decision-making processes right from the outset of any project.

what is the difference between devops and devsecops
DevOps has gained widespread popularity in the past decade, and its various definitions reflect its evolution. One commonly accepted definition characterizes DevOps as the integration of development and operations within a single organizational framework. This integration entails a shared responsibility for ensuring product quality and operational efficiency, fostering a collaborative environment that accelerates iteration and enhances value delivery to customers.
DevSecOps, a distinct yet interconnected concept, builds upon the foundation of DevOps by incorporating security objectives. Rather than being viewed as a separate entity, DevSecOps is considered a natural progression of DevOps, extending its principles to include security considerations. This evolution is characterized as incremental rather than revolutionary.
The introduction of the DevOps model brought about methodologies and tools that significantly increased development velocity. However, this accelerated pace created challenges for security teams, which struggled to keep up. While development processes became streamlined and automated, security measures remained static, often causing delays or relying on external teams for post-production security checks.
DevSecOps addresses these challenges by integrating security activities early in the Software Development Life Cycle (SDLC). This proactive approach ensures the identification and resolution of security issues during the application development process. By empowering development teams to independently handle security tasks, the model prevents security vulnerabilities from reaching production, ultimately reducing the costs associated with post-release flaw fixes.
A key feature of DevSecOps is the cultivation of a collaborative culture that aligns security efforts with the principles of DevOps, fostering scalability and efficiency. Automation plays a crucial role in this paradigm, as security measures are seamlessly integrated into every stage of the development pipeline. This holistic approach not only enhances the security posture of applications but also contributes to a more agile and resilient software development lifecycle.
What are the Key Elements for Implementing DevSecOps?
While each DevSecOps project possesses its distinct characteristics, there are fundamental elements that most organizations should incorporate to achieve successful DevOps implementation. The following are eight critical elements that we consider essential for the majority of organizations.
1. Container Security
As containers play a central role in contemporary DevOps workflows, they become a primary focus for DevSecOps initiatives. Container security encompasses three key dimensions:

- Image scanning: Docker images and base images may include numerous software components with outdated, unpatched, or vulnerable aspects. A DevSecOps approach involving containers should integrate image scanning and remediation at every stage of the CI/CD pipeline. Automated container image scanners guarantee that images exclusively contain stable and secure code, adhering to secure configuration best practices.
- Minimal base images: To minimize the attack surface, it is crucial to reduce the number of files and components within a container. Opting for a minimal base image and installing only the necessary libraries for the container’s functionality helps limit the attack surface, enhancing overall security.
- Container image risk management: This involves the identification of embedded secrets, software vulnerabilities, malware, and configuration defects within container images. A robust DevSecOps strategy addresses these risks, ensuring a secure and resilient container environment.
- Drift protection: To prevent configuration drift in containers, mechanisms should be in place to promptly identify and block malicious activities. Drift protection plays a pivotal role in maintaining the integrity of container configurations and responding swiftly to potential security threats.
2. Infrastructure Automation
Automation plays a pivotal role in DevSecOps by efficiently identifying and rectifying security vulnerabilities and configuration issues throughout the IT environment. Contemporary automation methods encompass:
- Configuration management: This process automates the deployment of resources using rigorously tested and secure configurations. It also oversees changes to configurations, ensuring that modifications do not introduce security vulnerabilities.
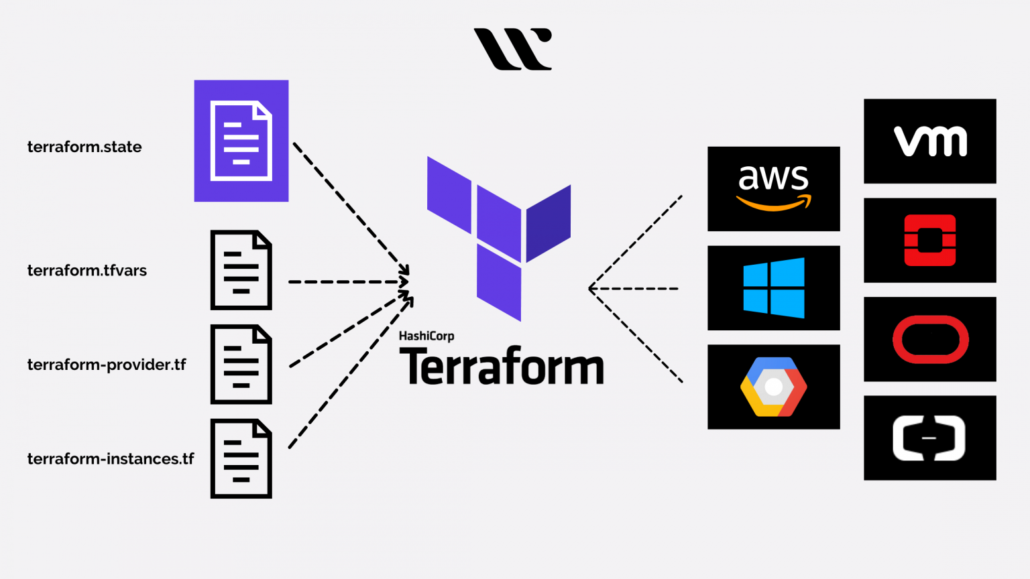
- Infrastructure as Code (IaC): Utilizing human-readable code templates, IaC defines the deployment specifications for environments. Automated provisioning of resources occurs based on these templates, allowing the incorporation of security measures into resources during deployment.
3. Application Analysis
Application analysis is crucial for identifying security issues, such as application vulnerabilities, early in the Software Development Life Cycle (SDLC) and addressing them before they escalate into complex and costly challenges. Various tools and technologies are employed in application analysis, including:

- Static application security testing (SAST): This method analyzes the source code to pinpoint issues related to code quality, non-secure coding practices, and known vulnerabilities.
- Software composition analysis (SCA): SCA scrutinizes third-party and open-source packages, along with their dependencies resolved during a build, to identify known vulnerabilities and potential conflicts with open-source licenses.
- Dynamic application security testing (DAST): DAST assesses running applications to uncover vulnerabilities that surface during runtime, along with other potential attack vectors.
- Interactive application security testing (IAST): Positioned between SAST and DAST, IAST utilizes source-level knowledge of the application structure to detect vulnerable conditions and attack vectors in compiled applications.
- Threat modeling: This approach facilitates the prediction, detection, and analysis of security threats by identifying the attack surface. By proactively minimizing exposure to identified risks, teams can enhance their ability to address potential security issues effectively.
4. Identity and Access Management
Identity and access management (IAM) comprises methodologies that utilize centrally defined policies to regulate access to data, applications, and other network assets. IAM should extend its governance over all facets of the DevOps environment, spanning each stage of the Software Development Life Cycle (SDLC). This comprehensive approach aids in preventing unauthorized access to sensitive systems and thwarting lateral movement.
IAM encompasses various methods, including:

- Authentication controls: These mechanisms verify the identity of a user or application.
- Authorization controls: These controls grant authorized users access to specific resources or functions.
- Role-based access controls (RBACs): RBACs provide a group of users access to a resource or function based on their responsibilities or collective permissions. This streamlines administration, onboarding processes, and mitigates privilege creep.
- Hardware security modules (HSMs): Physical devices like HSMs manage and safeguard secrets such as credentials, certificates, and keys, whether at rest or in transit.
- Identity providers (IdPs): These services handle user authorization, ensuring secure access to resources.
- Secrets vaults: These repositories store secrets and restrict access to only authorized users.
- Container image provenance and image signing: These functionalities validate the authenticity of container images, establishing trust in the integrity of the images.
5. Network Controls and Segmentation
Network controls and segmentation provide the means to visualize, segregate, and regulate traffic orchestrated by container orchestration tools. These controls are instrumental in isolating tenants and ensuring the secure flow of communication among components of containerized applications and microservices. Additionally, they offer the advantage of segregating development, testing, and production networks, safeguarding against the impact of attacks on one environment affecting others.
Methods employed for network control and segmentation include:
- Container orchestration network security policies: These policies enable the control of traffic flows at the IP address or port level. Implementing controls for cluster ingress and egress traffic, along with logging and network visualization, enhances both control and visibility.
- Software-defined networking (SDN): SDN ensures a programmable, adaptable network fabric that can be provisioned in real time to meet evolving business demands and security requirements.
- Service mesh: This technology provides automated network segmentation and visualization, along with authentication and authorization capabilities for container-based applications and microservices.
6. Data Controls
Data control methods and technologies play a crucial role in safeguarding data integrity and preventing unauthorized data leakage. These methods ensure protection for data at rest and in motion through:
- Data encryption: Utilizing symmetric and private key encryption, tokenization, and key management, these capabilities effectively thwart unauthorized exfiltration of data from databases, files, and containers.
- Data protection: This involves the detection and classification of sensitive data, implementing enhanced security controls to bolster regulatory compliance, and establishing monitoring and auditing capabilities. Access controls are initiated in development and testing environments to prevent compromise, thereby mitigating the risk of supply chain attacks. These controls extend to production environments, providing defense against service disruption and data exfiltration.
- Data masking: Techniques like data anonymization and pseudonymization are employed to offer realistic data for development and testing environments without compromising production data. This ensures a balance between the need for authentic testing scenarios and the imperative to protect sensitive information.
7. Auditing, Monitoring, and Alerting
Auditing and monitoring methodologies offer valuable insights into security incidents within production environments, facilitating faster incident response by providing detailed forensic information on potential causes and consequences. The components of monitoring include:
- Cloud-native monitoring tools: Examples like Prometheus and Jaeger enable the monitoring of distributed environments, featuring centralized log aggregation and support for the persistent storage of log data.
- Security Information and Event Management (SIEM): SIEM centralizes event reporting by consolidating log and network traffic data from distributed devices, endpoints, security tools, and applications.
- Forensics: This element provides in-depth insights into security vulnerabilities, offering evidence for compliance audits and expediting recovery efforts.
- Dashboards and visualization: These tools display security information, presenting trends and Key Performance Indicators (KPIs) in a manner meaningful for developers, operations, and security teams. For instance, a dashboard can illustrate the progression or regression of vulnerabilities or security incidents in a specific application over time.
- Alerting tools: These tools aid DevSecOps teams in promptly responding to security incidents. Ideally, an alert tool analyzes, prioritizes, and notifies the team of anomalies after verification as real incidents. This ensures that upon notification, the team can swiftly investigate and respond to the incident.
8. Remediation
In the event of a security incident within a production environment, tools are at the disposal to automatically implement corrective measures. This not only enhances uptime but also prevents the proliferation of threats within the environment. Another crucial aspect involves establishing traceability of production issues back to the specific build and code component responsible for the problem, allowing developers to swiftly address and remediate the issue.
Remediation components encompass:
- SOAR (Security Orchestration, Automation, Response): SOAR responds to security incidents by executing automated operations and integrating seamlessly with other security tools.
- Cloud Workload Protection Platforms (CWPP): CWPP continuously assesses cloud environments, identifies misconfigurations, and automatically rectifies them in accordance with security best practices.
DevSecOps Best Practices
Once you have confirmed the presence of the key elements outlined above, consider incorporating the following best practices to enhance the efficacy of your DevSecOps program.
Shift Security Left
A fundamental principle of DevSecOps involves the concept of shifting security left—conducting security tasks at the earliest stages of the development lifecycle. To fully embrace the DevSecOps approach, security experts must collaborate with developers during the planning and initial construction phases of a product. It is crucial for them to ensure the security of components, configurations, and environments. Additionally, providing developers with the necessary tools to validate the use of secure coding best practices and the utilization of only safe components and container images is essential.
Establish Continuous Security Controls
To ensure the effectiveness of DevSecOps, the automation of security controls is imperative. This allows the incorporation of security checks at every phase of the development pipeline, minimizing the risk of human error. Implementing automated tooling enables:
- Code scanning for identifying flaws and adhering to security best practices.
- Scanning of open-source components and container images.
- Verification of secure configurations and remediation of misconfigurations.
- Establishment of development, testing, and production environments with inherent security best practices.
- Utilization of orchestration for executing automated tasks in a consistent, repeatable, and auditable manner.
Integrate with CI/CD Pipelines
A CI/CD pipeline is constructed with the aim of identifying quality issues and establishing a rapid feedback loop for developers. In a DevSecOps environment, this principle extends to security:
- The CI/CD pipeline should autonomously and consistently employ security tools (as detailed in the previous section).
- The CI/CD pipeline serves as a comprehensive record of alterations to code, applications, and infrastructure. These modifications should be aggregated into metrics and reports accessible for scrutiny by security teams.
- Changes indicative of security issues or threats should prompt an incident response process.
- Security personnel should employ the same collaboration tools utilized by developers and operations (such as issue trackers and chat platforms) to collaboratively prioritize security issues for remediation.
Focus on Traceability, Auditability, and Visibility
For a DevSecOps process to achieve success, it should enable:
- Traceability: The capability to monitor changes in configuration and environment throughout the entire lifecycle, from planning to production.
- Auditability: The capability to automatically generate reports and documentation pertaining to development processes, inclusive of the associated security controls.
- Visibility: The capability to comprehend the operational landscape, identify security vulnerabilities and threats, and effectively respond to them.
By integrating these three capabilities, a development process can adeptly navigate an ever-changing threat landscape and fulfill rigorous compliance requirements.


