Introduction
DevSecOps, a fusion of Development, Security, and Operations, represents a methodology that ingrains security measures throughout every stage of the application or software development lifecycle. Its primary objective is to automate security protocols and reduce vulnerabilities, aligning with the security and compliance goals of both IT and business entities. By embedding security measures early in the development cycle and seamlessly integrating them with continuous integration, continuous delivery, and continuous deployment (CI/CD) pipelines, DevSecOps enables organizations to ensure the robust security of their applications.
Effectively implementing the DevSecOps approach involves leveraging various tools and strategies to detect and mitigate security risks. This article will delve into some of the most effective open-source DevSecOps tools available as of 2024.
DevSecOps Tools Categories

DevSecOps tools can be classified into distinct groups based on their functionalities. These categories encompass:
- Static Application Security Testing (SAST) Tools
- Dynamic Application Security Testing (DAST) Tools
- Software Composition Analysis (SCA) Tools
- Container Security Tools
- Infrastructure as Code (IaC) Security Tools
- Continuous Integration/Continuous Deployment (CI/CD) Security Tools
- Compliance and Governance Tools
- Security Dashboard and Analytics Tools
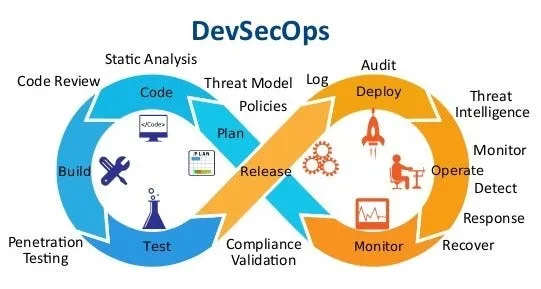
Top OpenSource tools DevSecOps for 2024
Software Composition Analysis (SCA) Tools:
OWASP Dependency-Check is a tool for analyzing software compositions, aiming to identify known vulnerabilities present in project dependencies.
Retire.js is a JavaScript library scanner designed to detect vulnerabilities in the libraries utilized within your web applications.
WhiteSource Bolt, an open-source Software Composition Analysis (SCA) tool, scans project dependencies to pinpoint known vulnerabilities and offers actionable remediation steps.
Dependency-Track, an open-source platform, actively monitors and tracks a project’s dependencies, providing valuable insights into their known vulnerabilities.
OSSIndex serves as an open-source vulnerability database and analysis platform. It seamlessly integrates with various development tools, delivering real-time security intelligence on project dependencies.
Static Application Security Testing (SAST) Tools:
SonarQube is an open-source platform dedicated to continuous code quality inspection. It incorporates static code analysis to identify security vulnerabilities in code.
Bandit is a security-focused Static Application Security Testing (SAST) tool designed specifically for Python. It scrutinizes Python code for common security issues and vulnerabilities.
SpotBugs, an evolution of FindBugs, serves as an open-source static analysis tool tailored for Java applications. It excels in detecting coding errors, potential vulnerabilities, and performance issues.
RIPS is an open-source PHP security analysis tool, specializing in identifying security vulnerabilities and coding flaws within PHP applications.
PMD, an open-source source code analyzer, supports multiple programming languages, including Java, JavaScript, and XML. It is adept at pinpointing potential bugs, dead code, and security vulnerabilities.
Dynamic Application Security Testing (DAST) Tools:
OWASP ZAP, or Zed Attack Proxy, stands as an open-source web application security scanner designed to assist in the identification of vulnerabilities within web applications.
Nikto, an open-source web server scanner, conducts thorough tests against web servers to uncover potential vulnerabilities.
Wapiti, an open-source web application vulnerability scanner, engages in black-box testing to audit the security of web applications.
Arachni, an open-source and modular web application security scanner, scrutinizes web applications for a broad spectrum of vulnerabilities and produces detailed reports.
Grabber, an open-source web application scanner, employs crawling and scanning techniques on web pages to detect security vulnerabilities.
Container Security Tools:
Clair is an open-source vulnerability scanner tailored for containers, focusing on analyzing container images and generating reports on identified vulnerabilities.
Trivy, another open-source vulnerability scanner, extends its coverage to containers and various artifacts like operating system packages and application dependencies. It conducts scans on container images and delivers comprehensive reports, detailing the severity of any detected vulnerabilities and suggesting remediation steps.
Anchore Engine, an open-source tool, specializes in analyzing container images to identify vulnerabilities, policy violations, and adherence to best practices.
Sysdig Falco is an open-source behavioral activity monitoring tool specifically designed for containers and Kubernetes environments. It actively detects and alerts on abnormal behavior and potential security threats in real-time, utilizing rules and policies to define expected container behavior and raising alerts when deviations occur.
Infrastructure Security Tools:
OpenSCAP stands as an open-source framework dedicated to compliance checking and vulnerability management, offering capabilities for assessing and securing infrastructure systems.
Lynis, an open-source security auditing tool, focuses on evaluating the security configuration of Linux and Unix-based systems.
Dagda, an open-source container security analysis tool, conducts static analysis of container images to identify and address security issues and vulnerabilities.
ScoutSuite, an open-source multi-cloud security auditing tool, assesses the security posture of containerized infrastructure within public cloud environments.
Compliance Tools:
OpenSCAP serves as a Security Content Automation Protocol (SCAP) framework, designed for tasks such as compliance checking, vulnerability management, and measurement.
OpenVAS, short for Open Vulnerability Assessment System, is a comprehensive vulnerability scanner proficient in detecting security vulnerabilities across systems and networks.
Wazuh, an open-source host-based intrusion detection system (HIDS), plays a key role in compliance monitoring, file integrity monitoring, and log analysis.
Dashboard Tools:
Grafana is an open-source platform for analytics and monitoring, enabling the creation of customizable dashboards to visualize a variety of metrics and data sources.
Kibana, an open-source data visualization dashboard, is specifically designed for Elasticsearch. It facilitates the exploration, analysis, and visualization of data stored in Elasticsearch indices.
Metabase, an accessible open-source business intelligence and analytics tool, empowers users to effortlessly create dashboards and visualize data from diverse sources.
Vulnerability Tracking Tools:
OWASP DefectDojo is an open-source vulnerability management tool designed to assist in tracking and managing vulnerabilities within your applications and infrastructure.
TheHive, an open-source platform for incident response and case management, incorporates features for effectively tracking and managing vulnerabilities.
Summary
In summary, open-source tools are pivotal in the realm of cybersecurity, offering diverse solutions across categories such as Software Composition Analysis (SCA), Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Container Security, and Infrastructure Security. These tools play a crucial role in identifying vulnerabilities, assessing security risks, and ensuring compliance.
It’s essential to recognize that the open-source tools landscape is dynamic, with specific tools’ availability and popularity subject to change over time. Maintenance and updates for open-source projects rely on community feedback and contributions, leading to varying levels of support based on community involvement.
While open-source tools provide valuable and cost-effective resources for cybersecurity, it is crucial to approach their selection and usage with a comprehensive understanding of their limitations and reliance on community support.



