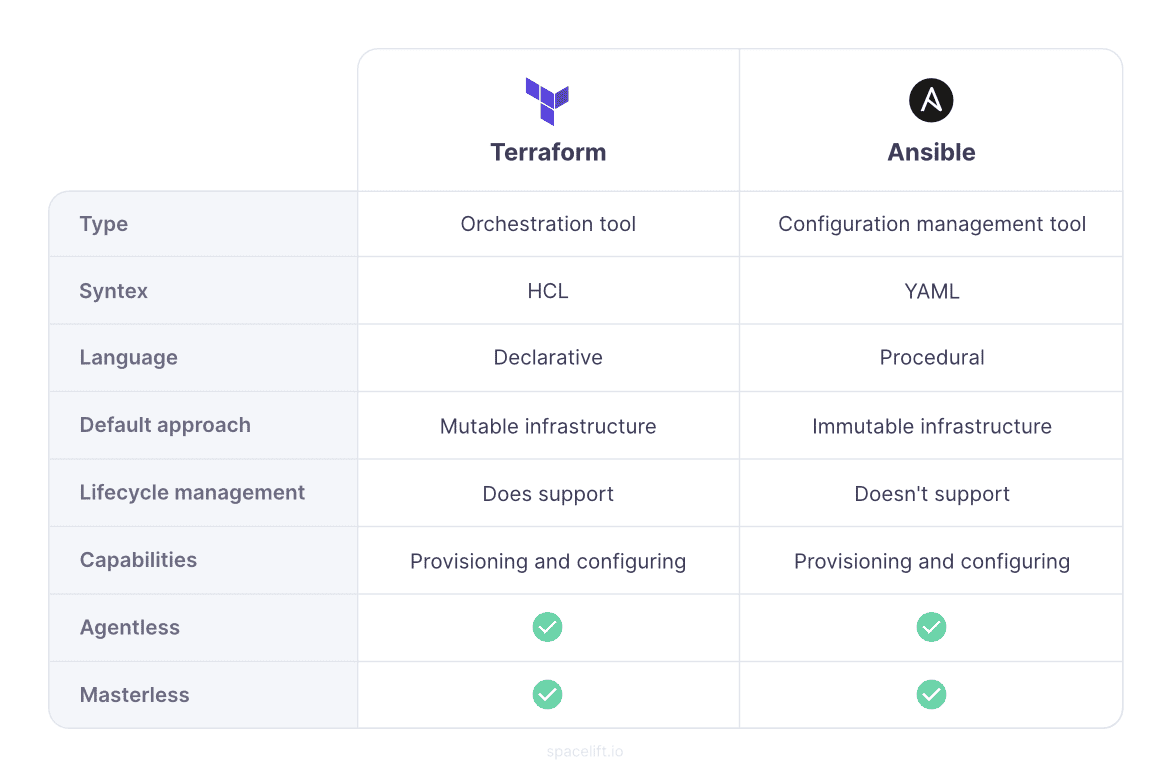
What sets Terraform and Ansible apart? Terraform specializes in orchestrating cloud infrastructure deployment, whereas Ansible excels in configuring that infrastructure once it’s provisioned.
When deciding between Terraform and Ansible, it’s essential to consider your specific needs and workflows. While Terraform is ideal for infrastructure provisioning, Ansible shines in managing configurations.
In this comparison, we’ll delve into the distinctions between Terraform and Ansible, identify common ground, and ultimately determine the optimal approach for infrastructure management based on real-world expertise.

What is Terraform?
Terraform empowers users to efficiently provision, manage, and deploy their infrastructure through a process known as Infrastructure as Code (IaC), facilitated by a declarative configuration language named HashiCorp Configuration Language (HCL). Originally developed by HashiCorp and distributed under an open-source license, Terraform has transitioned to a Business Source License (BUSL) model.
Key Attributes of Terraform:
- State Management: Terraform maintains a state file to keep track of resources and their configurations, enabling seamless management of infrastructure.
- Declarative Approach: Users articulate the desired state of their infrastructure using simple, human-readable code, leaving Terraform to execute and manage the necessary changes.
- Extensive Provider Support: With support for over 3,000 providers, Terraform offers unparalleled flexibility and compatibility, allowing users to interface with various cloud services, APIs, and infrastructure technologies.
- Modular Design: Leveraging a declarative language, Terraform facilitates the modularization of infrastructure configurations, promoting code reusability and maintainability across projects.
What is Ansible?
Ansible is a powerful software tool crafted for streamlining automation and orchestration tasks across various platforms, regardless of scale. It’s coded in Python and strongly supported by RedHat along with a dedicated open-source community. This command-line IT automation solution finds extensive application in configuration management, infrastructure provisioning, and application deployment scenarios.
Here’s a breakdown of Ansible’s key features:
- YAML: Ansible utilizes YAML, a straightforward and human-readable data format, facilitating easy comprehension and manipulation.
- Modules: These are reusable standalone scripts designed to execute specific tasks, enhancing the versatility and efficiency of Ansible’s automation capabilities.
- Playbooks: These YAML files articulate configurations, deployments, and orchestration sequences within Ansible. They can contain single or multiple plays.
- Plays: Plays, subsets within playbooks, delineate sets of tasks to be executed on specific hosts or host groups, allowing for granular control over automation workflows.
- Inventories: Ansible centralizes all machine-related information in a single, comprehensible file. This includes IP addresses, server details, databases, and other relevant data, facilitating streamlined management and organization.
- Roles: These are modular units of organization that simplify the sharing and reuse of automation code among users, fostering collaboration and efficiency within Ansible environments.
Ansible vs Terraform: Similarities
At a high level, Terraform and Ansible exhibit similarities in their capabilities. Both tools excel in provisioning new cloud infrastructure and configuring it with necessary application components.
They share the ability to execute remote commands on newly created virtual machines, rendering them agentless. This eliminates the need to deploy agents on machines for operational purposes.
Terraform leverages cloud provider APIs for infrastructure creation, while basic configuration tasks are accomplished using SSH. Similarly, Ansible utilizes SSH for its configuration tasks. Notably, the “state” information for both tools doesn’t necessitate a separate infrastructure for management, rendering them both masterless.
Differences Between Terraform and Ansible
The preceding section offers an overview of Terraform and Ansible, highlighting their fundamental similarities. Initially, it appears that both tools excel in provisioning and configuration management tasks. However, a closer examination reveals nuanced differences that favor one over the other in specific contexts.
In essence, both Terraform and Ansible possess strengths that make them valuable tools. They share common ground in managing infrastructure, which broadly involves orchestration and configuration management. Yet, each tool approaches these aspects differently, with varying strengths and weaknesses in their overlaps.
Therefore, it becomes imperative to scrutinize the finer details of both tools to determine the optimal choice or combination, delineating their respective boundaries for effective utilization.
1. Orchestration vs. Configuration Management
Orchestration and provisioning involve creating the foundational elements of a system, such as virtual machines, networks, and databases. In contrast, configuration management automates the setup and maintenance of software components, operating systems, and network configurations.
Terraform and Ansible are tools capable of handling both tasks, but they have distinct focuses. Terraform excels at managing infrastructure by leveraging cloud provider APIs to create and remove resources based on predefined configurations. On the other hand, Ansible is primarily tailored for configuration management, ensuring that applications and dependencies are consistently updated and configured.
While both tools are versatile, there are limitations to using Terraform for configuration management and Ansible for complex infrastructure automation. Terraform may lack the flexibility needed for intricate configuration tasks, while Ansible might struggle with orchestrating large-scale infrastructure changes.
In a logical sense, orchestration can be viewed as a “Day 0” activity, laying the groundwork for the system, while configuration management is more of a “Day 1” and ongoing task, ensuring the system remains properly configured and up to date. Therefore, Terraform is well-suited for initial infrastructure setup (Day 0), while Ansible excels at ongoing configuration management (Day 1 and beyond).
2. Declarative vs. Procedural Language
Terraform is a tool designed for writing Infrastructure as Code (IaC), utilizing the HashiCorp Configuration Language (HCL), which operates in a declarative manner. This means that the sequence in which the code is written doesn’t affect its functionality, and the code can be spread across multiple files without issue.
Regardless of how the code is structured, Terraform can discern dependencies and provision infrastructure accordingly. Transitioning existing infrastructure to code or crafting new infrastructure is straightforward with Terraform. If you’re interested in learning more about importing existing infrastructure into Terraform’s management, you can explore this Terraform import tutorial.
On the other hand, Ansible employs YAML syntax to define procedures for executing tasks on target infrastructure. Ansible YAML scripts follow a procedural approach, executing commands from top to bottom as written.
These scripts, known as “Ansible playbooks,” outline a series of tasks to be performed sequentially. For instance, if you need to install an Apache server on a specific virtual machine with root privileges, you must first create the user and then define the installation task within the playbook.
3. Mutable vs. Immutable Infrastructure
The process of deploying an application involves setting up the necessary infrastructure and installing the correct version of source code and dependencies on that infrastructure.
The concept of mutability pertains to how changes in applications and services are implemented within the underlying infrastructure. Deployment can occur either on existing infrastructure or by provisioning entirely new infrastructure for the same purpose.
Deployment practices play a crucial role in determining whether the infrastructure is mutable or immutable. In mutable infrastructures, newer versions of applications are deployed onto existing infrastructure. Conversely, in immutable infrastructures, deployment occurs on completely new infrastructure with each release.
While mutable infrastructures may seem convenient, they carry a higher risk of failure. This is because updating applications on the same infrastructure involves uninstalling the previous version and then installing the desired version, which introduces more steps and potential points of failure. This process can lead to inconsistent configurations and unpredictable behavior across a fleet of servers.
On the other hand, treating infrastructure as immutable involves reducing the number of steps by bypassing the uninstallation process and deploying onto new infrastructure resources. This approach allows for easier testing and rollback in case of deployment failures, providing greater control over changes.
There is no definitive rule dictating which approach is superior, as it depends on various factors.
Terraform excels in managing the lifecycle of infrastructure and better supports infrastructure immutability. It facilitates provisioning new infrastructure and deprovisioning older infrastructure seamlessly. However, managing configuration changes may not be as efficient with Terraform alone.
In contrast, Ansible specializes in configuration management and supports infrastructure immutability through features like VM image creation. However, maintaining additional images requires additional effort.
A recommended approach is to combine the strengths of both tools: Terraform for infrastructure management and Ansible for applying configuration changes. This strategy, often referred to as the Blue/Green deployment strategy, reduces the risk of configuration failures and ensures smoother deployments.
4. State Management
Terraform orchestrates the entire lifecycle of resources it manages, maintaining a crucial mapping of infrastructure resources to their current configurations in state files. This state management aspect is fundamental to Terraform’s functionality.
States serve the purpose of monitoring configuration changes and facilitating the provisioning process accordingly. Additionally, Terraform allows for the incorporation of pre-existing resources into its management system through the importation of real-world infrastructure into state files.
At any given point, querying Terraform’s state files provides insight into the current infrastructure components and their respective attributes.
In contrast, Ansible lacks built-in lifecycle management capabilities. With its focus primarily on configuration management and a default preference for immutable infrastructure, any modifications to the configuration are automatically applied to the target resource without explicit lifecycle management features.
5. Configuration Drift
Configuration drift occurs when there’s a misalignment between the intended configuration and the actual configuration of your system. This discrepancy often arises when changes are made directly to the system by engineers or automated processes, bypassing the defined configuration management tools. For instance, if you use Terraform to define your infrastructure but manually tweak settings outside of it, you introduce drift.
Addressing drift is crucial, and tools like Spacelift’s drift detection not only identify discrepancies but can also automatically correct them if desired.
While both Ansible and Terraform aim to tackle drift, they do so through different approaches. Ansible employs idempotent tasks and continuous execution, avoiding the need for persistent state tracking. In contrast, Terraform relies on a stored state to detect and manage drift, advocating a declarative style in managing infrastructure as code.
Conclusion
The debate between Terraform and Ansible often leads to the question: “Which one is better?” The answer isn’t straightforward and lies in understanding their strengths. Terraform excels in orchestration, while Ansible shines in configuration management. Although they can perform each other’s tasks to some extent, their primary strengths lie in their designated areas. Therefore, it’s advisable to utilize both tools for infrastructure management, leveraging their individual strengths effectively.



